The Role of Top Management in Developing Security and Safety Culture in the Organization (A Case of Enterprise Group)
Abstract:
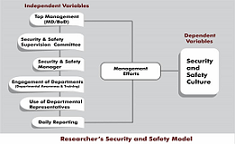
The study investigated the role top management play in developing security and safety culture in the organization. Specifically, a case study exploration was used to evaluate one primary area of interest: 1. the role top management plays in developing organization’s security and safety culture. The strategy used for this work was exploratory, with both qualitative and quantitative approaches since the data collected would be converted into numerical value for better interpretation. The target population was the staff of Enterprise Group in the Greater Accra Region of Ghana, and the sample was composed of 30 management and staff members, using convenience sampling. Primary and secondary sources of data were used in this study. A survey questionnaire was used to acquire information from the target management and staff of Enterprise Group Ltd. The data gathered was analyzed quantitatively by using descriptive statistical tables and percentages where the Chi-Square test was considered. Statistical package for social sciences (SPSS) version 25 software was also used in the analysis. The study concluded that top management plays a role in developing security and safety culture in organizations through Security and Safety Supervision Committee, by building enabling security and safety working environment in organizations, ensuring there are policies and procedures guidelines in place in organizations. When there is Daily Reporting and available systems to address non-compliance issues in the organization to develop security and safety culture among employees. it is recommended that the Government and regulatory bodies of organizations should emphasize the establishment of security and safety policies in organizations.References:
[1] Korletey, E. N., Asare, E. B., & Teye, J. K. (2019).
The Role of the Labour Department in International Labour Migrant Management in
Ghana. Journal of Economics, Management and Trade, 1-15.
[2] World Health Organization. (2010). World health statistics
2010. World Health Organization.
[3] Raelin, J. A. (2016). It’s not about the leaders: It’s
about the practice of leadership. Organizational Dynamics, 45(2).
[4] Newell, B. R., & Shanks, D. R. (2014). Unconscious
influences on decision making: A critical review. Behavioral and Brain Sciences,
37(1), 1–19.
[5] Herath, T., & Rao, H. R. (2009). Encouraging information
security behaviors in organizations: Role of penalties, pressures and perceived
effectiveness. Decision Support Systems, 47(2), 154–165.
[6] Colgan, P. A., Boal, T., & Czarwinski, R. (2013). Requirements
relating to radon in the International Basic Safety Standards: information, measurement
and national strategies. Journal of Radiological Protection, 33(1), 41.
[7] Sadgrove, K. (2016). The complete guide to business risk
management. Routledge.
[8] Pinsonneault, A., & Kraemer, K. (1993). Survey research
methodology in management information systems: an assessment. Journal of Management
Information Systems, 10(2), 75–105.
[9] Armstrong, M. (2006). A handbook of human resource management
practice. Kogan Page Publishers.
[10] Christopher, L., Choo, K.-K., & Dehghantanha, A. (2017).
Honeypots for employee information security awareness and education training: a
conceptual EASY training model. In Contemporary Digital Forensic Investigations
of Cloud and Mobile Applications (pp. 111–129). Elsevier.
[11] Shaw, R. S., Chen, C. C., Harris, A. L., & Huang, H.-J.
(2009). The impact of information richness on information security awareness training
effectiveness. Computers & Education, 52(1), 92–100.
[12] Singer, P. W., & Friedman, A. (2014). Cybersecurity:
What everyone needs to know. OUP USA.
[13] Blanchard, P. N. (2006). Effective Training, Systems, Strategies,
and Practices, 4/e. Pearson Education India.
[14] Camp, L. J. (2009). Mental models of privacy and security.
IEEE Technology and Society Magazine, 28(3), 37–46.
[15] Puhakainen, P., & Siponen, M. (2010). Improving employees’
compliance through information systems security training: an action research study.
MIS Quarterly, 757–778.
[16] Kohn, A. (1999). Punished by Rewards: The Trouble with
Gold Stars, Incentive Plans, A’s, Praise, and Other Bribes. Houghton Mifflin Harcourt.
[17] Coopey, J. (1995). The learning organization, power, politics
and ideology introduction. Management Learning, 26(2), 193–213.
[18] Glendon, A. I., & Stanton, N. A. (2000). Perspectives
on safety culture. Safety Science, 34(1–3), 193–214.
[19] Brown, W., & Nasuti, F. (2005). Sarbanes-Oxley and
enterprise security: IT governance-what it takes to get the job done. Information
Systems Security, 14(5), 15–28.
[20] Sennewald, C. A., & Baillie, C. (2015). Effective security
management. Butterworth-Heinemann.
[21] Furnell, S., & Clarke, N. (2005). Organizational security
culture: Embedding security awareness, education, and training. Proceedings of the
IFIP TC11 WG, 11, 67–74.
[22] Martins, E. C., & Terblanche, F. (2003). Building organizational
culture that stimulates creativity and innovation. European Journal of Innovation
Management, 6(1), 64–74.
[23] Downs, C. W., & Adrian, A. D. (2012). Assessing organizational
communication: Strategic communication audits. Guilford Press.
[24] Bedford, T., Cooke, R., & others. (2001). Probabilistic
risk analysis: foundations and methods. Cambridge University Press.
[25] Annan, K. A. (2005). In larger freedom: towards development,
security and human rights for all: report of the Secretary-General. United Nations
Publications.
[26] Hofstede, G., Neuijen, B., Ohayv, D. D., & Sanders,
G. (1990). Measuring organizational cultures: A qualitative and quantitative study
across twenty cases. Administrative Science Quarterly, 286–316.

